“Data is your organization’s most valuable asset – but who can access it? That’s where things get tricky.”
TL;DR
Problem: Broad permissions overexpose data, while fine-grained controls are hard to manage at scale, risking security and efficiency in OneLake.
Solution: OneLake RBAC enables folder-level access control, enhancing security and streamlining collaboration.
Future: Expect broader RBAC features, unified access models, and AI-driven automation for seamless data governance.
With enterprises moving to cloud-based platforms like Microsoft Fabric’s OneLake, managing access to files and folders in Lakehouses is critical. Misconfigured permissions can lead to data breaches, compliance violations, and disrupted workflows. That’s why understanding Role-Based Access Control (RBAC) in OneLake isn’t just important – it’s essential for protecting sensitive data and ensuring seamless collaboration across your teams.
Data Chaos Without Proper Access Control
Managing access in data platforms can quickly become overwhelming due to the intricate layers of permissions required to balance collaboration and security. Organizations often struggle with:
- Coarse-Grained Access and Over-Provisioning: Granting broad access risks exposing confidential data. For example, OneLake allows workspace-level access roles like Admin, Member, Contributor, or Viewer, which apply to all items within a workspace, including all files and folders in a Lakehouse. In addition, item permissions such as Lakehouse provide access to the entire Lakehouse, including all folders and files. Of the three types of permissions available (ReadData, ReadAll, or Build), it is ReadAll that grants access to all data in the Lakehouse. If a workspace includes both sales and finance data in its Lakehouse, assigning access at the workspace or Lakehouse levels, can unnecessarily expose sensitive information to unintended teams.
- Fine-Grained Access and Challenges: Restricting access too much can hinder productivity and delay projects. Sharing individual files within a Lakehouse provides fine-grained control but poses challenges. Each file requires manual permission settings, which can become unmanageable at scale. For enterprises with extensive data assets and large-scale teams, this process is time-intensive, increases the likelihood of inconsistencies, and complicates maintaining uniform access policies. These issues often result in administrative burdens and security vulnerabilities, especially as organizations scale their collaborative efforts.
Insider risks further illustrate the need for effective data access management. In 2023, insider errors caused 55% of incidents, costing $505K per case, while malicious insiders cost $701K. On average, containment took 86 days, with delays pushing costs to $18.3M+. Financial services faced the highest impact at $20.68M annually (DTEX 2023).
Organizations require a smarter, centralized solution that ensures the right people access the right data at the right time, while seamlessly balancing flexibility and security for collaborative efforts.
OneLake Role-Based Access Control (RBAC)
RBAC is a structured method of managing data access by assigning users or groups to predefined roles. These roles determine permissions, ensuring users can only access the data necessary for their tasks. This approach reduces the risk of unauthorized access while streamlining management and maintaining operational efficiency.
Microsoft Fabric introduces the preview feature of OneLake Data Access Roles. It allows administrators, contributors, and members in the workspace to define roles applying read permissions to specific folders within a Lakehouse. Users who are granted access can view only authorized folders when navigating through the Lakehouse UX, notebooks, or APIs.
RBAC solves the problem by providing:
- Granular Permissions: Enables tailored access by defining roles and assigning them to specific folders. This granular permission model improves security by supporting the principle of least privilege, ensuring users only access the data they need.
- Centralized and Efficient Management: Simplifies access control by managing all permissions from a single point, ensuring consistency across the organization while minimizing administrative overhead. This avoids micromanagement of individual files and promotes secure collaboration.
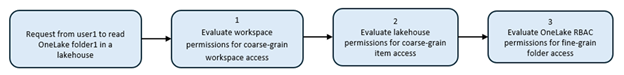
How Permissions Are Evaluated
When a user requests folder access, Fabric first checks workspace and lakehouse permissions for broad access. OneLake RBAC is then applied to enforce fine-grained, folder-level restrictions, ensuring secure and precise data control.
Get started with OneLake RBAC
- Enable RBAC for a Lakehouse
Open the target Lakehouse in Fabric and click Manage OneLake data access (preview) from the ribbon. In the confirmation dialog, select Continue to enable the feature (note that you must be an Admin, Member, or Contributor to proceed). Upon enabling, a “DefaultReader” role is created, granting read access to existing users. If you need to restrict access, delete this role or remove the ReadAll permissions from users. - Create and Assign Roles
Select New Role and name it. Choose whether to apply the role to all folders or select specific folders by checking the boxes next to the relevant folders. After defining the role, click Assign role, add users or groups, and save the configuration to enforce folder-level access control. Additionally, use the Add users based on Lakehouse permissions option to dynamically grant access based on existing permissions (e.g., ReadAll, Write). Virtual members are automatically added to the role and can only be removed by adjusting their Fabric permissions.
Note: If users already have higher permissions (e.g., write access) through their workspace role (such as Member), a warning symbol will appear next to their name, indicating their elevated access level.
- Edit Roles
Hover over the role you want to modify, select it, and adjust folder permissions or user assignments as needed. Make sure to save the changes to apply them. - Delete Roles
Navigate to Manage OneLake data access (preview), check the boxes next to the roles you want to remove, and confirm the deletion.
Case Study: How OneLake RBAC Solves Real-World Challenges
Case Study: OneLake RBAC in Action
Scenario:
A retail company stores finance and sales data in the same Lakehouse. Finance needs confidential access to records, while sales requires performance data. Some shared datasets, like revenue reports, are essential for both teams.
Problem: Workspace-level permissions gave broad access to all data, exposing sensitive financial records to the sales team. Manual file sharing became inefficient and inconsistent as the organization scaled.
Solution: The company used OneLake RBAC to apply folder-level permissions:
- Finance Role – Access to financial records (e.g., tax documents, payroll).
- Sales Role – Access to sales data (e.g., forecasts, customer metrics).
Shared folders with joint data, like revenue summaries, were accessible to both roles.
Results:
- Enhanced Security – Financial data was protected from unauthorized users.
- Efficiency – Folder-level permissions reduced manual access management.
- Compliance – Improved data privacy and minimized internal fraud risks.
Beyond RBAC – Hidden Challenges
While OneLake RBAC offers powerful tools for securing and managing data access, it introduces complexities that organizations must be aware of to ensure effective data management.
- Shortcut Permission Limitations: OneLake RBAC permissions cannot be directly applied to shortcuts within a Lakehouse. Instead, permissions must be defined on the target folder where the original data resides. If a shortcut in a Lakehouse points to a table in a data warehouse or KQL database, access depends on the ReadAll permission of the Lakehouse. This complicates managing access pathways and enforcing consistent security policies.
- Inconsistent Permissions Across Interfaces: Data access roles apply only to users accessing OneLake directly. Fabric items like SQL analytics endpoints, semantic models, and warehouses use separate security models, leading to discrepancies. For example, a user without role-based permission to read certain tables may still access them by executing SELECT statements via SQL analytics if separately permitted, resulting in inconsistent access.
- Highest Permission Wins: If a user belongs to multiple roles, the highest permission level applies. This can unintentionally broaden access, potentially exposing sensitive data.
To mitigate these challenges, organizations should regularly audit permissions across OneLake, SQL analytics endpoints, semantic models, and shortcuts. This ensures consistency, prevents unintended data exposure, and avoids under-provisioning. Continuous reviews of overlapping roles help address the ‘highest permission wins’ issue, while limiting the use of nested roles reduces unnecessary access. Clear documentation of the differences between OneLake RBAC permissions and other Fabric security models are essential for maintaining secure and efficient access management.
Future Outlook
OneLake RBAC capabilities are anticipated to evolve into a more comprehensive access control system, extending beyond read-only permissions to include full write and management functionalities. The vision for the future is a unified access model that bridges gaps between OneLake RBAC, SQL analytics endpoints, and semantic models, resolving permission discrepancies and fostering seamless collaboration. Integration with external data sharing is expected to become more fluid, breaking down current limitations and enabling dynamic, secure data exchange. AI-driven automation may play a pivotal role, streamlining role assignment, predicting access needs, and minimizing administrative overhead to enhance operational efficiency.
OneLake RBAC secures data with folder-level control, preventing overexposure and simplifying large-scale access management. How will your organization leverage OneLake RBAC to protect its most valuable data?
References
- OneLake security overview
- Get started with OneLake data access roles (preview)
- Secure Data with Fabric, Compute Engines, and OneLake
- Role-based access control (RBAC)
- https://www2.dtexsystems.com/insider-risk-investigations-report-2023

Nafisa Ahmed
RDP Data Scientist


